
Member-only story
How to Deploy and Configure Azure Firewall with Terraform
Azure Firewall is a managed, cloud-based network security service that protects our Azure Virtual Network resources. It is a fully stateful firewall as a service with built-in high availability and unrestricted cloud scalability.
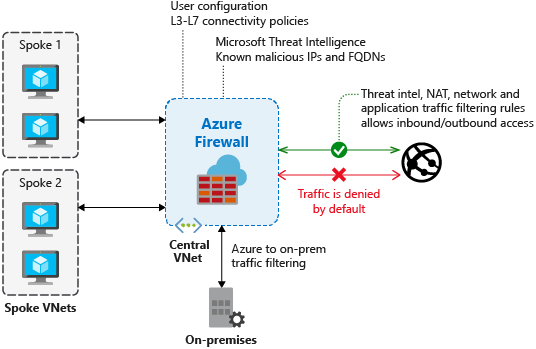
In this story, we will learn how to deploy and configure an Azure Firewall using HashiCorp Terraform.
On a typical Azure Cloud Hub-Spoke (aka Star) Architecture, we will use a Core or Shared VNET or Subscription, used to connect with on-premises and to provide shared services to production and non-production VNETs or Subscriptions.
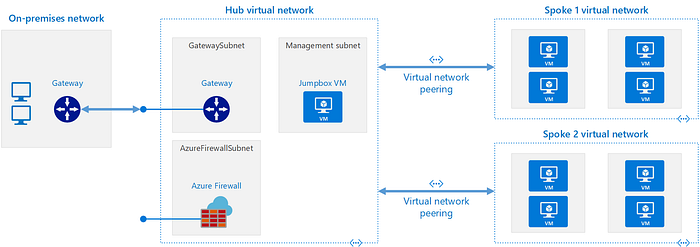
It is common to deploy an Azure Firewall inside this Core/Share VNET or Subscription to protect the inbound and outbound traffic between all VNETs or Subscriptions and the internet.
1. Creating the Core Network Resources with Terraform
We will need to create a Resource Group for our core environment.
We create a new Terraform file called main.tf and we add the following code:
# Create a resource group for core
resource "azurerm_resource_group" "core-rg" {
name = "kopicloud-core-rg"
location = "north europe"
tags = {
environment = "Core"
}
}Then, we add the code to create the Core VNET:
# Create the core VNET
resource "azurerm_virtual_network" "core-vnet" {
name = "kopicloud-core-vnet"
address_space = "10.10.0.0/16"
resource_group_name = azurerm_resource_group.core-rg.name
location = azurerm_resource_group.core-rg.location
tags = {
environment = "Core"
}
}and the Subnet for the Azure Firewall:
Note: The Subnet used for the Firewall must have the mandatory name AzureFirewallSubnet and requires at least a /26 subnet size.
# Create a subnet for Azure Firewall
resource "azurerm_subnet"…